ESET NOD32 ANTIVIRUS SERIAL KEYS 05/02/2012
Microsoft Security Compliance Manager - Review

Key Features and Benefits
• Central management of portfolio and benchmark: The central management console Security Compliance Manager provides a consistent user experience from beginning to end plan to design and security baselines for export. The tool gives you full access to a wide range of recommended baselines for Windows ® client and server operating systems and Microsoft applications. The Security Compliance Manager, you can quickly update the latest versions of Microsoft Basic and take advantage of version control base.
• Baseline Security Customization: Customization, comparing, merging, and reviewing baselines you never been easier. Now you can adapt the new ways of Security Compliance Manager one of the baselines, duplicate recommended by Microsoft for the Windows client and server operating systems and Microsoft applications quickly and change security settings to meet the environmental standards of your organization.
• Capacity to export multiple baselines for export to formats such as XLS, Policy Object (GPO), the desired configuration management (DCM), or packages Security Content Automation Protocol (SCAP) for automating the deployment and compliance tracking database.
• The baseline of security for Windows Server 2008 R2, Windows Server 2008, Windows Server 2003 Hyper-V, Windows 7, Windows Vista, Windows XP, the BitLocker Drive Encryption, Windows Internet Explorer 8, Microsoft Office 2010 and Microsoft Office 2007 SP2
• The recruitment pack for Windows 7, Internet Explorer 8
System Requirements
• Supported operating systems: Windows 7, Windows Vista Service Pack 2
• This toolkit is designed to work with System Center Configuration Manager 2007 and Desired Configuration Management (DCM) function.
• Microsoft Office Compatibility Pack for Word, Excel file formats, and PowerPoint (free download) can be used to open, edit and save documents, workbooks, and presentations in the file formats new to Microsoft Office 2007.
• Microsoft Word or Microsoft Word Viewer (free download) can be used to view Word documents.
The Security Compliance Manager-Start Guide is available on the official Microsoft site. Download this guide in order to adapt quickly and Security Compliance Manager (SCM) tool. The guide also includes a brief tutorial on using the CMS tool to implement and monitor security, the basis for the last server and client operating systems from Microsoft.
Tips to becoming a Computer Technician

How to Scan and Fix Registry with Registry Cleaner Software?

The computer has to remember many things - the material enclosed system options selected applications around, etc. Each time you use it, it has to go through all these entries. It can also be valid, missing or duplicate entries to be. This can be caused by the removal of something a predetermined material, deleting a file or program.
If such a case, you will find that the PC starts to work much slower than before. Although it through all these items in a very fast going, but it may take some time to read, even if there are. Finally, you see some programs refuse to run, and system crashes occur more frequently.
Of course you can always delete your computer to an expert for all the useless entries. It can, however, comes with a hefty price tag. It will also be conducted at regular intervals to keep your computer in top shape. Doing things on your own is certainly not advisable, as you yourself can lead to irreversible damage.
What you can install and run the registry cleaner software. This is done automatically on each of the entries from the first day. It safely and effectively remove those who are already invalid, missing or have been counted twice. This is a much safer way for you to do, rather than trying to manually delete entries that can cause PC problems.
You can scan and repair registry with the free software that you can find online. By downloading, read the system requirements so that you have something to install what is best for your computer will work. In addition, ensure that you get a reputable site. There are also the ones that you buy, often with other tools may be useful. Personally, I could clean my computer by downloading a software cleaner high quality recording.
New Server LeechBiz.com - Fast and unlimited premium link generator - Free

New Server LeechBiz.com - Fast and unlimited premium link generator - Free
Plugins: 33 Plugins
Premium Accounts : hotfile.com, rapidshare.com, depositfiles.com, uploading.com, mediafire.com, alldebrid, fast-debrid, debridmax
File size limit: 1024 MB
Get Paid To Complete Free, Fast and Easy Internet Tasks at MinuteWorkers.com - Turning Your Minutes Into Money - Work from home online and make money for free
It is called MinuteWorkers.com and here to can get paid for doing fast misc stuff on the Internet (basically do something you already do – register on forums, digg or stumble various websites).
MinuteWorkers a place where your minutes are exchanged for money. Complete a minute job and recieve money it's that simple! Work from home and earn free money today.
Featured Services:
-Earn Money Online Today
Complete short tasks and receive real money.
-Earn from Forum post and make threads
The rates
New Post: $0.01
New Thread: $0.01
Per reply to your thread: $0.01
-Free $1.00 bonus to employers
Try the service for free and employ 10 workers at no cost.
-Create a workforce in seconds
create tasks which can be completed by the 1000's of workers.
-Invite your friends and earn more
One referral/affiliate system allows you to earn up to $0.15 per sign up.
-Cashout
AlertPay and Paypal
minimum Cashout $2.00
----------------------------------------------------------------
Youtube Explination Video
Keywords:minute,workers,minuteworkers,work from home,work from home online,free cash,easy money,easy money online for free,how to make easy money online for free,make easy money online for free
Eset Nod32 Antivirus Username Password 30/01/2012
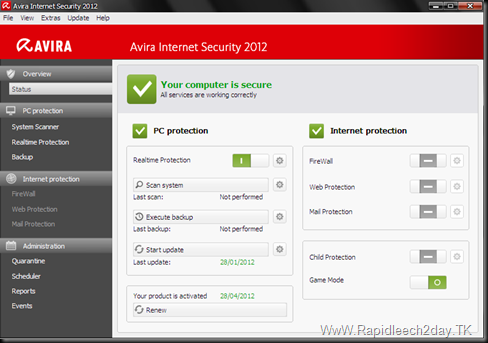
Download Avira Internet Security 2012 Latest Version with new key/license valid until 28-4-2012 + VDF Update
Avira Internet Security 2012 Latest Version with new key/license + VDF Update | 137.2 MB
Choose Internet Security 2012 if you:
Regularly look up information on the web
Access your bank accounts or investments online
Shop in online stores or place bids at auction sites
Make online phone calls, instant message or social network
Use public wifi networks
Store your irreplaceable photos, music and videos on your PC
Are concerned about what your children might see and do online
-Configurable Game Mode You can choose to suspend update notices and other nonessential messages while gaming or watching movies.
-Express Installation
We’ve taken the guesswork out of setup: No confusing options or Q&A, just antivirus that gets it right the first time.
-Faster startup and performance
Version 2012 is leaner on system resources than ever before. That means both faster scanning and less waiting while booting up.
-Better Protection
We’ve hardened all components to outfox new forms of malware that escape traditional virus scanning methods.
-Better Repair Functionality We’ve updated our repair technologies to provide the most effective removal of malware – and any traces it leaves behind.

--------------------------------
Avira Internet Security 2012 Latest Version with new key/license + VDF Update | 137.2 MB
Internet Download Manager (IDM) 6.08 Build 9 Final Full - Working 100% + Multilingual – Preactivated - Silent Installation Released: Jan 26, 2012

Internet Download Manager (IDM) 6.08 Build 9 Final - Working 100% + Multilingual – Full Cracked – Preactivated - Silent Installation increases download speed Size: 5.36MB
Internet Download Manager increases download speed with built-in download logic accelerator, resume and schedule downloads
(Released: Jan 26, 2012)- Added support for new types of video streaming sites
Internet Download Manager (IDM) is a tool to increase download speeds by up to 5 times, resume and schedule downloads. Comprehensive error recovery and resume capability will restart broken or interrupted downloads due to lost connections, network problems, computer shutdowns, or unexpected power outages.
Simple graphic user interface makes IDM user friendly and easy to use.Internet Download Manager has a smart download logic accelerator that features intelligent dynamic file segmentation and safe multipart downloading technology to accelerate your downloads.
Unlike other download managers and accelerators Internet Download Manager segments downloaded files dynamically during download process and reuses available connections without additional connect and login stages to achieve best acceleration performance.
Home Page: http://www.internetdownloadmanager.com
IDM is multilingual. IDM is translated to Arabic, Bosnian, Bulgarian, Chinese, Croatian, Czech, Danish, Dutch, French, German, Hungarian, Italian, Japanese, Lithuanian, Macedonian, Polish, Portuguese, Romanian, Russian, Slovenian, Spanish, Thai languages.
Internet Download Manager (IDM) 6.08 Build 8 Final + Multilingual – Full Cracked – Preactivated - Silent Installation increases download speed Size: 5.36MB
Installation instructions:
1. Download Internet Download Manager Now / Uninstall oldest version – reboot OS
2. Unrar and run exe file (just double click)
3. Run Internet Download Manager (IDM) from your start menu
4. Have fun!



Nod32 antivirus 4 username and password 25/01/2012
Download Media Player Classic - Home Cinema 1.5.3.3996 is a free audio and video player for Windows XP,Vista,7 32bit/64bit. latest version free 21 Jan 2012 Freeware

Media Player Classic - Home Cinema 1.5.3.3996 - 11.3 MB
Media Player Classic - Home Cinema is a free audio and video player based on Media Player Classic. Many new features have been integrated in this player.Some features of Media Player Classic Home Cinema 1.5.3.3996:
- Option to remove Tearing.
- Support for EVR (Enhanced Video Renderer)
- Supports Subtitles.
- Playback and recording of television if a supported TV tuner is installed.
- Creation of minidump when MPC HC crashes.
- OSD (On Screen Display)
- Shuttle PN31 remote control support
- Support for Multi-Monitor configuration
- Pixel shader to convert BT601 - BT701
- YV12 Chroma Upsampling pixel shader
- Language Translations.
Supported Decoding:
MPEG-1, MPEG-2 and MPEG-4 playback. Media Player Classic is capable of VCD, SVCD and DVD playback, without the need to install any additional software or codecs.
It has built-in codecs for MPEG-2 video and codecs for LPCM, MP2, AC3 and DTS audio, and also contains an improved MPEG splitter that supports playback of VCDs and SVCDs using its VCD/SVCD/XCD Reader. A *.mp4 and MPEG-4 Timed Text support added. An AAC decoding filter makes MPC suitable for AAC playback in MP4.
MPC Home Cinema also has H.264 and VC-1 with DXVA support, DivX, Xvid, and Flash Video formats is available in MPC HC. MPC can also use the QuickTime and the RealPlayer architectures. Media Player Classic supports native playback of OGM and Matroska container formats.
Supported Video, Audio and Image file formats:
WAV, WMA, MP3, OGG, SND, AU, AIF, AIFC, AIFF, MIDI, MPEG, MPG, MP2, VOB, AC3, DTS, ASX, M3U, PLS, WAX, ASF, WM, WMA, WMV, AVI, CDA, JPEG, JPG, GIF, PNG, BMP, D2V, MP4, SWF, MOV, QT, FLV.
Media Player Classic - Home Cinema supports the following operating systems:
- Windows XP SP3 32bit/64bit
- Windows Vista 32bit/64bit
- Windows 7 32bit/64bit

Rapidleech Server v3.45.Stable Release 17-1-2012 -133 Plugins Premium Accounts :fileserve, filesonic With all Options – Rar/Unrar, Movie Thumbnailer and more..
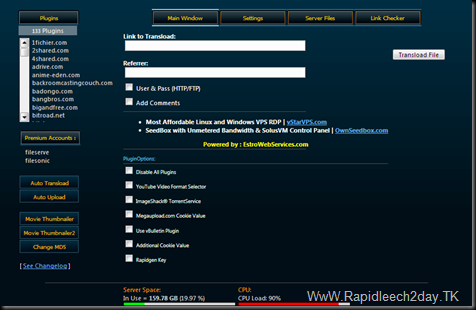

Rapidleech Server v3.45.Stable Release 17-1-2012 -133 Plugins Premium Accounts :fileserve, filesonic With all Options – Rar/Unrar, Movie Thumbnailer and more..
Have Fun!
Eset nod32 antivirus username and password 21/01/2012
Internet Download Manager (IDM) 6.08 Build 8 Final - Working 100% + Multilingual – Full Cracked – Preactivated - Silent Installation Increases Download Speed

Internet Download Manager (IDM) 6.08 Build 8 Final - Working 100% + Multilingual – Full Cracked – Preactivated - Silent Installation increases download speed Size: 5.36MB
Internet Download Manager increases download speed with built-in download logic accelerator, resume and schedule downloads
(Released: Jan 17, 2012)- Redesigned video stream recognition for web players. Added support for new types of video streaming sites
- Added support for Filesonic changes
- Fixed bugs
Internet Download Manager (IDM) is a tool to increase download speeds by up to 5 times, resume and schedule downloads. Comprehensive error recovery and resume capability will restart broken or interrupted downloads due to lost connections, network problems, computer shutdowns, or unexpected power outages.
Simple graphic user interface makes IDM user friendly and easy to use.Internet Download Manager has a smart download logic accelerator that features intelligent dynamic file segmentation and safe multipart downloading technology to accelerate your downloads.
Unlike other download managers and accelerators Internet Download Manager segments downloaded files dynamically during download process and reuses available connections without additional connect and login stages to achieve best acceleration performance.
Home Page: http://www.internetdownloadmanager.com
IDM is multilingual. IDM is translated to Arabic, Bosnian, Bulgarian, Chinese, Croatian, Czech, Danish, Dutch, French, German, Hungarian, Italian, Japanese, Lithuanian, Macedonian, Polish, Portuguese, Romanian, Russian, Slovenian, Spanish, Thai languages.
Internet Download Manager (IDM) 6.08 Build 8 Final + Multilingual – Full Cracked – Preactivated - Silent Installation increases download speed Size: 5.36MB
Installation instructions:
1. Download Internet Download Manager Now / Uninstall oldest version – reboot OS
2. Unrar and run exe file (just double click)
3. Run Internet Download Manager (IDM) from your start menu
4. Have fun!


Nod32 antivirus 4 username and password 17/01/2012
Password: dfbuahr5ht
For versions: ESS / EAV
Username: TRIAL-59008560
Password: ahp4jrdsx7
For versions: ESS / EAV
Username: TRIAL-59008603
Password: v5b8hen47n
For versions: ESS / EAV
Username: TRIAL-59009761
Password: p68dcd3n3u
For versions: ESS / EAV
Username: TRIAL-59009802
Password: 3f66jv2n47
For versions: ESS / EAV
Username: TRIAL-59008182
Password: e8cpsarf8d
For versions: ESS / EAV
Username: TRIAL-59008268
Password: nck3pnb3pb
For versions: ESS / EAV
Username: TRIAL-59008342
Password: 68r3j2b5du
For versions: ESS / EAV
Username: TRIAL-59008392
For versions: ESS / EAV
Username: TRIAL-59008448
Password: tmm48m46a2
For versions: ESS / EAV
Username: EAV-57927561
Password: p84fucjv26
For versions: EAV
Valid until :2012 -07-15
Username: EAV-57933924
Password: j5a3f3c37d
For versions: EAV
Valid until :2012 -07-15
Username: EAV-57874662
Password: sr5km4ar8f
For versions: EAV
Valid until :2012 -07-15
Username: EAV-57874553
Password: jh2h5s8sk5
For versions: EAV
Valid until :2012 -07-14
Tim Tebow, not God, Throws the Ball
That's just to be on the team. To be a first-string quarterback, you have to be the best of the best.
Tim Tebow is such a man. He worked extraordinarily hard to get where he is ... which is why Tim Tebow's religion is a real shame. Christianity has stolen Tebow's pride. Instead of taking pride in his accomplishments, he gives the credit away to God. The simple fact is that it's Tebow throwing the ball, not God.
In less than a second or two, Tebow's mind absorbs the receiver's position, speed and direction, and on top of that he includes the position and momentum of each opposing player. Tebow instantly calculates how the receiver can elude the opponents to arrive at an open position, then hurtles the pigskin ball down the field with incredible accuracy of direction, altitude and velocity. And it's not just that one receiver; he simultaneously has to choose between several receivers, runners, running it himself, or throwing the ball away.
That is talent. Tebow deserves to take pride in his skill. But instead, Tebow gives his accomplishment away. Tebow believes there's a god out there who alters the laws of physics of the universe because this god, who created the unimaginably vast universe, cares whether the NFL team called the "Denver Broncos" wins or loses. And the reason this god cares is because Tebow presumably prays more earnestly than the opposing quarterback.
What's wrong with pride in one's accomplishments? Christians, Jews and Muslims count pride as one of the big sins. Why? Having pride in one's work is admirable. Pride makes us do our best and then lets us take pleasure in a job well done.
That is what Tebow should be doing rather than thanking God.
Several years back I wrote a blog about this same topic (except that it was about friends and family) that is still one of my favorites. I closed it with this:
Religion lets people avoid personal responsibility by asking, and getting, God's forgiveness. Never mind whether the victims agree with God. I suppose that's a pretty good bargain – "Believe in me, and you're off the hook for your sins." But the flip side of the deal is that God also steals all the glory. Everything good is God's doing. Humans get all the blame, and God gets all the credit.
Nod32 antivirus 4 username and password 13/01/2012
Password: pd2nu5thpt
For versions: ESS / EAV
Username: TRIAL-58767996
Password: nrhc5hren7
For versions: ESS / EAV
Username: TRIAL-58768023
Password: 6r4ebett4m
For versions: ESS / EAV
Username: TRIAL-58768074
Password: phuere4e53
For versions: ESS / EAV
Username: TRIAL-58766627
Password: 3atk3peve8
For versions: ESS / EAV
Username: TRIAL-58766688
Password: bfxp365a52
For versions: ESS / EAV
Username: TRIAL-58766748
Password: rferrujaf3
For versions: ESS / EAV
Username: TRIAL-58766796
Password: x43k75sms3
For versions: ESS / EAV
Username: EAV-57798149
For versions: EAV
Valid until :2012 -07-13
Username: EAV-57798152
Password: v67pn5xvej
For versions: EAV
Valid until :2012 -07-13
Username: EAV-57798147
Password: sfrk4tb5v2
For versions: EAV
Valid until :2012 -07-13
Download MCS Drivers Disk 9.0.40.450 - x86/x64 (ENG/RUS/FR 2012) Full – automatically detects Free


Supported operating systems: Windows 2000
WindowsXP 32/64 bit
Windows2003 32/64 bit
Windows Vista 32/64 bit
Windows 2008 32/64 bit
Windows 2008 R2 32/64 bit
Windows 7 32/64 bit
Defined devices:
Chipset
Video
Audio
NIC and PCI modems
HDD Controllers
IEEE 1394 Host Controller
USB Host Controllers
CardBus controllers
USB Devices
LPT printers
Serial external modems
PCMCIA devices
Some common ACPI device.
Number of drivers found by the program for one or Ina OS depends on the availability of those on the disk (limited by disk space) and the correct ways of filling in the appropriate configuration files. Users can add or remove drivers from the disk and add to the HWID.
This program was written for himself and friends, and accordingly provided As Is (as is). Drivers on the disc have not been tested for compatibility with all operating systems for which they are declared. The author is not liable for any damage caused by using the program.
- Updated database devices.
- Utilities updated to the newest versions.
- Components updated to v9.20 7Zip
- Updated language files.
- Updated some drivers to the newest versions.
- Many other changes and bug fixes.

Yahoo! Messenger 11.5.0.155 Latest Version Final 2012 – Full Offline installer – Free Instant messaging allows you to quickly exchange messages with your online friends



Requirements:
Windows 2000 / XP / 2003 / Vista / Windows7 / XP64 / Vista64 / Windows7 64
License: Freeware
Date added: January 11, 2012

God Burns Widow's House, But Saves His Own Stuff
"A family is counting their blessings tonight after an early morning fire in Dearing, GA destroyed most of their home. But one pretty special item was left unscathed ... Bernice Hunt's Bible was pulled from the ashes without a charred edge or a burnt page. The only damage at all was a little moisture from the fire hoses."So let me see if I get this. God decided to burn this woman's house to the ground. He let all of her possessions go up in smoke. She already lost her husband, has cancer, and had open-heart surgery ... presumably God was responsible for all of that too.
So what 'miracle' does God perform for this poor, sick widow? He saves his own Holy Bible from the flames!
I mean, after all, it is His own word, isn't it? I guess if I were God and was going to burn down a sick widow's house, I'd want to get my stuff out first.
The real mystery is how thoroughly this attitude about God pervades Judeo-Christian-Islamic thinking. It's automatic: some massive catastrophe comes along and causes death, destruction and grief, but somewhere there's a tiny random fluctuation in events that spares a baby or a bible, and that is the miracle.
God, as usual, gets all the credit and none of the blame.
Eset Smart Security 5 Serial Keys 08 January 2012
Password: r6un3k6sp6
For versions: ESS / EAV
Username: TRIAL-58462059
Password: 4anr6kdapc
For versions: ESS / EAV
Username: TRIAL-58462134
Password: pn335t4t4h
For versions: ESS / EAV
Username: TRIAL-58463346
Password: 5n2ru53x5k
For versions: ESS / EAV
Username: TRIAL-58463411
Password: 82v6hefbxh
For versions: ESS / EAV
Username: TRIAL-58463758
Password: pba7akp6r7
For versions: ESS / EAV
Username: TRIAL-58463722
Password: rab8srcksj
For versions: ESS / EAV
Username: TRIAL-58463987
Password: 6pkk75mat6
For versions: ESS / EAV
Username: TRIAL-58465545
For versions: ESS / EAV
Username: TRIAL-58465657
Password: drufrfkma7
For versions: ESS / EAV
Serial Keys: TRIAL-58463812
Password: rxsfcmhr4k
For versions: ESS / EAV
Eset Keys: TRIAL-58463848
Password: pxretfub38
For versions: ESS / EAV
Username: TRIAL-58463890
Password: sn6j2jtphe
For versions: ESS / EAV
Username: TRIAL-58463936
activation code: eehbm6r746
For versions: ESS / EAV
(File Fetch) Convert Filesonic, Fileserve, Hotfile and Megaupload links to direct download links eg. mediafire, jumbofiles – Free

With File Fetching you can convert any of files stored on Megaupload to Mediafire or jumbofiles.
Supported file hosts: Filesonic, Fileserve, Hotfile and Megaupload.
eg.

Simply follow the instructions
First, you must Share the post on Facebook, so that others may enjoy it.
Share on Facebook
- Like us on Facebook ;
- Post this on your wall:
“Convert Megaupload links to direct download for free at http://rapidleech2day.tk > http://goo.gl/7OnMk"Make sure everyone can see it:

-----------
And then send links to elsa3dyads@gmail.com
Limits:
- 5 links per day.- Max file size 200MB per file mediafire – 400MB Filesonic, Fileserve, Hotfile and Jumbofiles.
And I will send you the direct links at most within 3 hours Or less than that if I online.
Have Fun!, Merry Christmas.
Web Security Threats To Look Out For

Exploiting news events - Hackers use stories as to trick users
Barely 24 hours after the announcement was the death of Qaddafi, we released that targeted malware that exploit the curiosity to see the history of big news began to be transmitted. Cybercriminals use human interest - and big news stories of the world as they generate a huge amount of hedging activities and the Internet. The same thing happened when bin Laden is dead, and when the royal wedding took place - and the trend will continue. The same trick is Halloween and other seasonal stories used, we saw many of these occur on social networking sites and others. Social engineering attacks to convince users to download content to the alleged event that is infected with new strains of malware related. Any event that is of interest and the interest generated is used to spread malware scams, fraud and other.
Insecurity browsers and plug-ins - only with Windows Update is not enough
Although your favorite web browser and operating system can be saved and corrected, the reality is that most people do not update plug-ins. Java, Adobe Flash and Adobe Reader plug-ins are often outdated and there are Web exploits that use this weakness to infect networks. Web exploits that specifically target this vulnerability (such as the Black Hole exploit kit) are increasingly popular in the cyber-criminals.
Compromised high profile Webs and "drive-by downloads"
So how to distribute these vulnerabilities? The first method is "fast flux" sites, sites that are created solely for the purpose of distributing malware for a short time. The second way is to compromise a site level and the injection of a "drive-by download" - a piece of code that infects a user when they have a website (there is no need of anything, click here - just visit the site of infection is the user's computer - so that drive-by). Usps.gov the site and the site were exposed to mysql.org these two types of attacks.
There is a third method of spreading these infections. Instead of using a website, send a malware authors content on Web advertising companies infected. This content is then passed on thousands of websites with these promotional affiliates, and each site hosting the ads is to spread malware, and this code is detected. The London Stock Exchange was a website that exposed to these types of attacks this year, even though it was by far not the only way.
Search Engine Poisoning
End users have become accustomed to rely on search engines. They (wrongly) believe that the well-known search engine like Google or Bing would never directly on a website that is infected with malicious software. But search engines do not really make a difference between sites, the search results according to their ranking algorithms. As a result of malware authors are flooding search results with links to the pages of bait to take the user to download malicious websites, malicious software on their computers. As users became more suspicious you are certain types of links, this type of search image search now, the most difficult to avoid are moved.
Evolve as Internet threats, it is more difficult to ignore exposed to the threat posed by the user browsing the Internet, and further develop as an attack, you must ensure that your Web browsing activity n ' is not so expect more than you.
Fake Antivirus Scams and Android Users

Windows systems have been the prime target for scam scareware. But now, with the use of explosives of the mobile device, said Denis Maslennikov Kaspersky Lab researcher that online fraudsters have started for users of mobile devices with Android offers similar viruses and false fake anti-virus software. Write on the blog SecureList Maslennikov said that Web search turns to popular mobile applications, such as the mobile version of Opera Web browser, are fraudulent sites offer "free" for viruses from devices phones, including Android.
As scareware scam for users of Microsoft Windows, the results are predictable free scans.
"Both parties argue that the user device may be infected, and someone verify access to personal data and then ask the user to the device for malware."
A scan of the camera returns hard-coded "positive" results and encourages the user to the mobile device to "activate" the protection of the safety of the device by clicking on a link in the scan results. Click here to download and install a malicious application that Kaspersky detects Trojan-SMS.AndroidOS.Scavir for Android.
Attacks against mobile devices are becoming more common as users shift their preferences from desktops and laptops, mobile phones and tablets.
ESET Smart Security 5 Claves 03 January 2012
Password: 2nhvkjpebk
For versions: ESS / EAV
Username: TRIAL-58152096
Password: 2p7pfedskb
For versions: ESS / EAV
Username: TRIAL-58152135
Password: hjdrsu4ab8
For versions: ESS / EAV
Username: TRIAL-58152178
Password: sxrprscct8
For versions: ESS / EAV
Username: TRIAL-58147874
Password: 7t4msfcjsx
For versions: ESS / EAV
Username: TRIAL-58148919
Password: rjm86ds66b
For versions: ESS / EAV
Username: TRIAL-58148956
Password: ex3jms65kt
For versions: ESS / EAV
Username: TRIAL-58149040
Password: 4ndas8d757
For versions: ESS / EAV
Username: TRIAL-58152246
For versions: ESS / EAV
Username: TRIAL-58152317
Password: 46dj2fesxj
For versions: ESS / EAV
Username: TRIAL-58152367
Password: 7sem85xar8
For versions: ESS / EAV
Username: TRIAL-58152418
Password: 5pfsnv64j5
For versions: ESS / EAV
Username: TRIAL-58152455
Password: evnv6jht87
For versions: ESS / EAV
Donate Me
Top 5 Anti Virus Software Packages Review – Spyware and Virus Cleaner
Finding the Best Anti-virus software and Malware Removal?
There are a few online sites that offer good reviews of the virus in the best and most popular spyware removers and cleaning programs. With so many different things online download option would be worth the time to learn to how each works. In the digital age of today, it is very common for typical users have their computers infected with malicious files.
Top 5 Anti Spyware and Anti Virus Software Review:
No Adware Software
It is the protection program, which recognize me and to eliminate all threats and malicious files, which helped my system infected PC before. The scan tool is one of the most advanced among all the others on the market and is able to offer a real-time protection. It can also detect, find files by e-mail to more if they threats before they open contain.
Adware Alert
Another protection program to get rid of this can alert the virus called adware and adware. You can program it to run a frequent corrections scan (d, regular analysis of all files. It is also with the ability to automatically update and generate alerts when new patches are designed to be available.
Spyware Remover
This software deals with malware before they are activated and damage to your computer system. It also helps the user to online sites and programs to determine if they authenticate to open safe.
Spyware Nuker
Netcom3 a particularly well-designed user interface and provides functions for real-time scanning. However, the detection and scanning speed may be slower than other software.
Netcom3
This is another software automatically updates itself and is a potent blocker of keyloggers, spyware, adware and other forms of malware in general.
Antivirus Protection – Free, Trial or Licensed Version?
Currently, there are many opportunities for security programs, which are manufactured by different companies. The most common anti-virus programs now Avast Anti Virus, AVG Anti-Virus, Avira Antivirus, BitDefender, ClamWin, ESET NOD32, Kaspersky Antivirus, McAfee Antivirus, Panda Antivirus and Norton Anti Virus. It is highly recommended that computer users have anti-virus programs to install in their systems. However, the choice to install the version you need to know the advantages and disadvantages.
There are no further security applications. they are really free to download. but the installation of free anti-virus program has its drawbacks. Not all free anti-virus products are updated. Thus, the most capable, without anti-virus software does not recognize recognize and identify new viruses and malware. The databases are in some versions of the free movement of anti-virus updated.
In addition to free versions of antivirus and security applications, there is also a trial version of antivirus products. Trial versions are made so that users can evaluate the products. Trial of anti-virus products are updated more free versions of antivirus software. However, trial versions of antivirus software usually takes 30 days only. Then you need to download another antivirus product or buy the licensed version of the software malware protection.
When selecting an antivirus solution firewall software for your computer, it is important to understand the advantages and disadvantages of choosing a free version or a trial or licensed version of the program you want to use.
SpyHunter 4.7.2.3687 - IKU - Brief Review

Here are some key features of Spy Hunter are:
- Removes spyware, adware, keyloggers, cookies, spyware registry keys, toolbars, internal popup programs, memory resident spyware
- Rollers capacity back to the distance to undo the spyware.
- Remove spyware programs that slow your computer
- Database of 500 spyware and adware
- The fastest scanner on the market (timed vs other products)
- Free updates when new spyware parasites
- Interface simple (to be as simple as a child's toy) use
- New! Compact integrated OS SpyHunter to remove rootkits and other malware parasites help the rebels.
New! Guards system to identify and stop all processes that attempt tosecretly Auto-Start-malware entries using the Windows registry.
- New! Exclusions feature allows you to exclude certain programs from being detected in future scans SpyHunter.
- Interactive one-on-one customer service called Spyware HelpDesk.
- New spyware definitions daily update added to ensure complete protection against the latest malware trends.
- Easy to use interface with intelligent automatic protection.
-Custom malware specific corrections to your computer for spyware Spyware HelpDesk problems.SpyHunters create a diagnostic report, sent to isanalyzed of our technicians, and a custom automated fix generated fromthe report to you on SpyHunter.
Download Parted Magic V11.12.30 with Programs 2012 Final – The Linux Live CD/USB Partitioning Free Tool - no install required - Open Source
 Parted Magic 2012 V2011-12-30 - Size: 181 MB
Parted Magic 2012 V2011-12-30 - Size: 181 MBFeatures
- Format internal and external hard drives.
- Move, copy, create, delete, expand & shrink hard drive partitions.
- Clone your hard drive, to create a full backup.
- Test hard drives for impending failure.
- Test memory for bad sectors.
- Benchmark your computer for a performance rating.
- Securely erase your entire hard drive, wiping it clean from all data.
- Gives access to non-booting systems allowing you to rescue important data.
- Runs from the CD, no install required.
- Partition programs.
- File System Tools.
- Booting Loader Tools.
- X Utilities
- Console Utilities
Parted Magic 2011_12_30 CD, USB, and PXE linux 3.1.6-pmagic
Added progeams: cifs-utils-5.2 and keyutils_1.5.2.
Screenshot


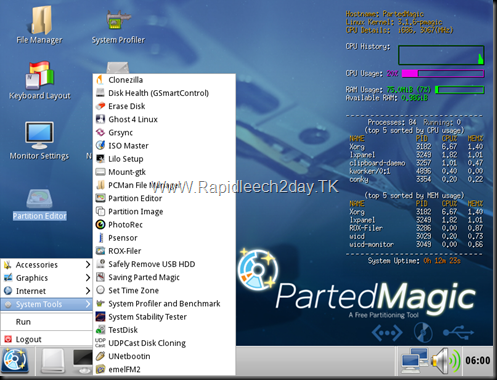
Size: 181 MB
License: Freeware

So Sorry Your Dad Died – Too Bad He's Burning in Hell
Now it happens that most of my relatives and close friends aren't Christian. We're a broad assortment of Deists, pantheists, paganists, agnostics and atheists. There's hardly a Christian among us.
So what do Christians write in their condolences? "The peace of the Lord is on your father." Or, "Your mother is resting in Jesus' arms now."
I know they mean well. But if these Christians were true to their faith, they'd say, "So sorry that your loved one is now being tortured with indescribable pain that is perpetually searing the flesh from her bones. I'm saddened that she will be screaming in agony for the rest of eternity. She seemed like such a nice lady. Too bad she didn't believe in Jesus."
Eternal cruel, sadistic, horrifying torture – that's true Christianity. Never mind that my loved ones are, to the last one, kind and moral people. I can't think of one family member or close friend who isn't a decent human being, and an asset to family, friends, community and humanity. They're good mothers and fathers, sisters and brothers, sons and daughters, friends and neighbors. They work hard and support themselves and their families. They vote in elections (mostly). They give back far more than they take in life.
But none of that matters. Most of my close friends and family don't accept the two-thousand-year-old myth that a woman was impregnated by God and had a son, who was actually God himself, who then arranged to have himself tortured to death, but he didn't really die and came back to life for a few more days, and then he died, except that he still didn't die because God pulled his son (who was really himself) up to heaven. And if you believe this story, all your sins are forgiven, no matter how horrible, but if you don't, all your good deeds are for nothing.
So it's pretty offensive when, in our grief over the death of a loved one, some well-meaning Christian writes about how the dearly departed is now in Jesus' arms or basking in God's glory. It's dishonest.
Christians who are offering kind thoughts to grieving friends should stick to a secular message. "I'm so sorry for your loss" would be just fine.





